BEWARE OF FAKE CHROME UPDATE
- SecneurX Threat Analysis

- May 3, 2023
- 3 min read
SecneurX Analysts found a Fake Chrome Update. Recently Malware authors used the compromised website to display fake Google Chrome automatic update errors and download a malicious file “update.exe” as an update if you visit them. This is done by injecting a js file on the compromised website which gets executed when the user visits the website.
This Binary file “update.exe” is a xmrig coinminer that does various actions when you execute them. Coinminer is an unwanted malicious software that uses the victim's computational power (CPU and RAM mostly) to mine for coins. To understand it's behaviour, we have analysed the sample in our Sandbox Environment an observed that, once the update.exe gets installed, the malware executes the following tasks

Process Injection Technique
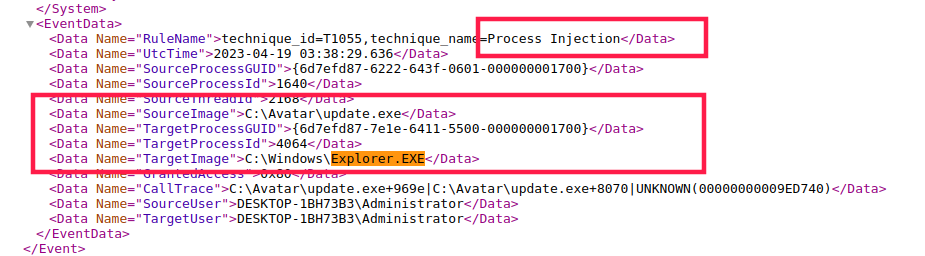
The malware copied itself to C:\ProgramFiles\Google\Chrome as "updater.exe" and then launched a legitimate executable to perform process injection and ran straight from memory. Here the malware used explorer.exe for process injection
Living Of The Land Attack

Then the malware added two exclusion paths to Windows Defender to prevent it from scanning the specified directories.

As the Threat Actor, their way of doing the Persistence Technique is one of the MITRE ATT&CK Adversaries. The above screenshot explains that the malware had scheduled a task.
Disabling Windows Defender and halting Windows services


The above command checked if the current user is an Administrator on a Windows system. If the user is an Administrator, it uses the "schtasks" command to run a task named "GoogleUpdateTaskMachineQC". If the user is not an administrator, it runs the updater.exe file in the Google Chrome location "C:\Program Files\Google\Chrome”.
After all these steps, the miner connected to the coin-miner domain and started mining the hard-to-trace cryptocurrency Monero (XMR).
IOC
Domain
xmr[.]2miners[.]com
IP
162[.]19[.]139[.]184
SHA256
2afdcf74d9dbc5575de919e8d041fc06c15044da0844fe9326b8f1b4bedad291
What can you do to avoid being a malware victim? Download applications from reliable sources. Be wary of programs that ask for unnecessary permissions or have suspicious reviews. Keep your devices and operating systems up to date to reduce the risk of attackers exploiting vulnerabilities.
Scrutinize emails & their attachments before opening them
Be wary of emails from unverified sources. You can check by communicating directly with the purported sender to confirm if they sent the messages. To check its validity, you can use SecneurX Sandbox to verify the sanity of the email.
Avoid clicking embedded links found in unverified emails
Such social engineering tricks can lead to the download of ransomware. Additionally, be wary of sites that prompt you to enter a CAPTCHA code as this could be linked to a ransomware attack. To check its validity, you can use services like SecneurX Sandbox to verify the site's reputation.
Back up your important files
While prevention is always better than cure, having a backup of important files can at least lessen the potential damage done by a malware attack. While being locked out of your own system is always a bad thing, at least it's not a total disaster since you can always retrieve your important files. The 3-2-1 backup rule applies here—three backup copies of your data on two different media and one of those copies in a separate location.
Regularly update software, programs, and applications
Updating them to the latest versions can provide an added layer of protection against online threats as malware and some ransomware arrives via vulnerability exploits.
Use a layered protection suite
Doing so can detect threats before they enter your network. Security solutions like SecneurX ATP can block Infectious files (like executables (.exe, .run, etc.), archives (ZIP, RAR, etc.), Microsoft Office and PDF documents, JavaScript, and so on) by scanning them at the point of entry of the organizations (File uploads, USB file transfers, etc)



Security researchers at SecneurX uncovered a clever fake Chrome update campaign: attackers injected a JavaScript into compromised sites that shows bogus Google Chrome update prompts and tricks visitors into downloading a file named “update.exe.” That binary is actually an XMRig coinminer malicious software that hijacks CPU and RAM to mine cryptocurrency so anyone who runs it will see degraded performance and unauthorized resource use. Even professionals like a Law essay writer surfing the web can fall victim if they accept the fake prompt, which is why vigilance and updated endpoint protection are essential. We sandboxed and analyzed the sample: once installed, the miner persists, spawns mining processes, and connects to remote wallets to quietly siphon compute power.